System Settings
Two-Factor Verification
Introduction
The enterprise backend contains a large amount of sensitive user information. Two-factor verification can provide deeper security protection for Dify Enterprise system administrator accounts. After enabling this feature, even if the original password is accidentally leaked, unauthorized access operations can still be prevented, ensuring the security of system administrator accounts and enterprise backend data. This mechanism requires users to enter a real-time verification code generated by an authenticator application after entering the correct password to complete login. This “two-factor” verification significantly improves account security.Implementation Prerequisites
Before configuring two-factor verification, please ensure the following conditions are met:- System Administrator Permissions - Only system administrators can configure two-factor verification.
- Authenticator Application - Install a compatible authenticator application on your mobile device.
Authenticator applications (such as Google Authenticator) are based on the TOTP (Time-based One-Time Password) standard and generate a new verification code every 30 seconds.
Enable Two-Factor Verification
Before enabling global two-factor verification for the team, ensure that two-factor verification has been configured for personal accounts.Personal Account
Steps to configure personal two-factor verification:1
Access Admin Backend
Log in to the Dify Enterprise admin backend.
2
Open Two-Factor Verification Settings
In the sidebar menu, click the “Two-Factor Verification” option.
3
Configure Authenticator
Find the authenticator section and click the “Configure” button on the right.
4
Scan QR Code
Use your authenticator application to scan the displayed QR code.
5
Enter Verification Code
Enter the six-digit verification code displayed by the authenticator application in the verification box to complete setup.
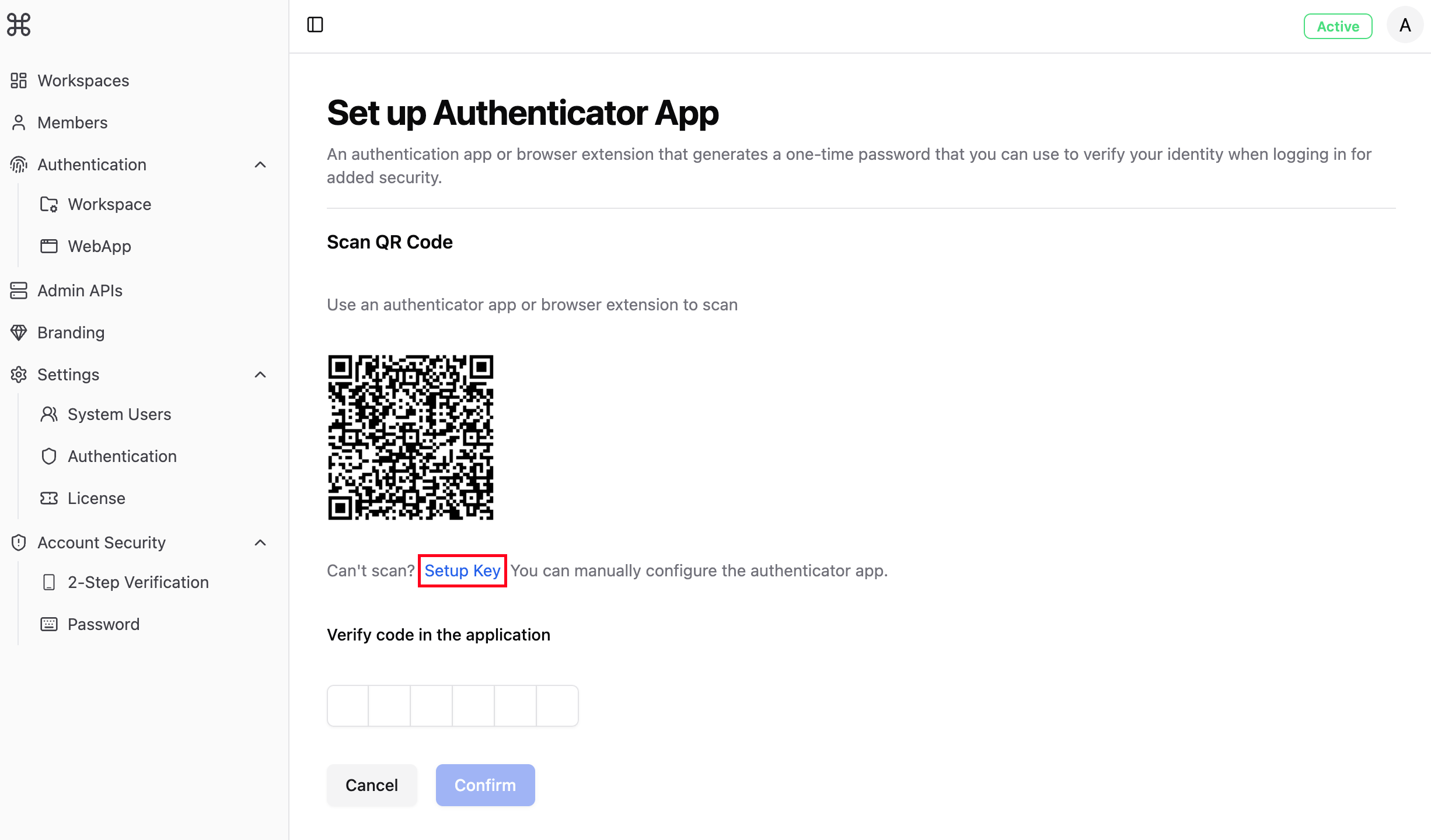 After enabling two-factor verification, backup codes will be generated simultaneously. To avoid being unable to obtain online verification codes due to loss of the device with the authenticator, it is recommended to handwrite or print backup codes in a safe place.
After enabling two-factor verification, backup codes will be generated simultaneously. To avoid being unable to obtain online verification codes due to loss of the device with the authenticator, it is recommended to handwrite or print backup codes in a safe place.
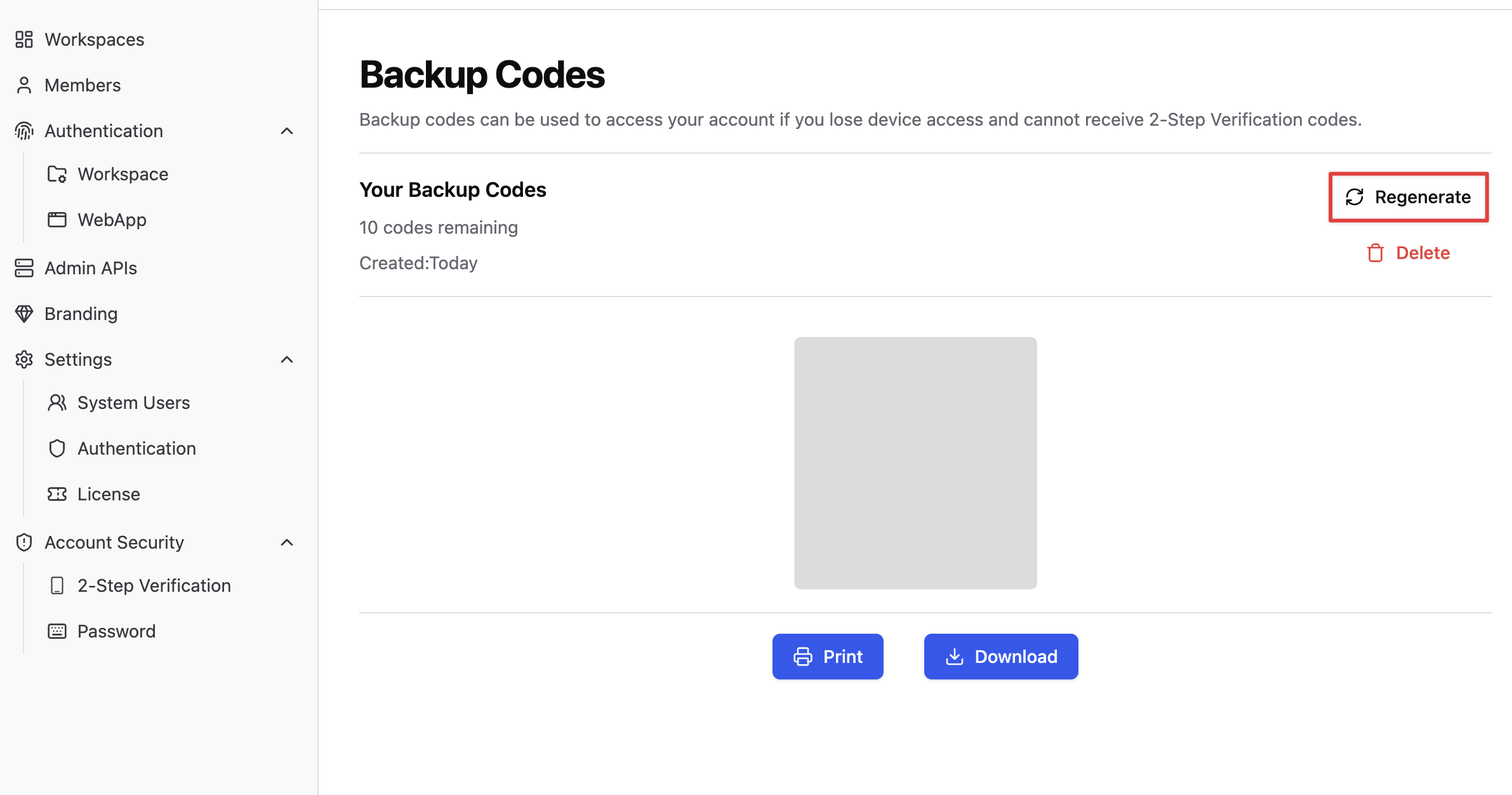
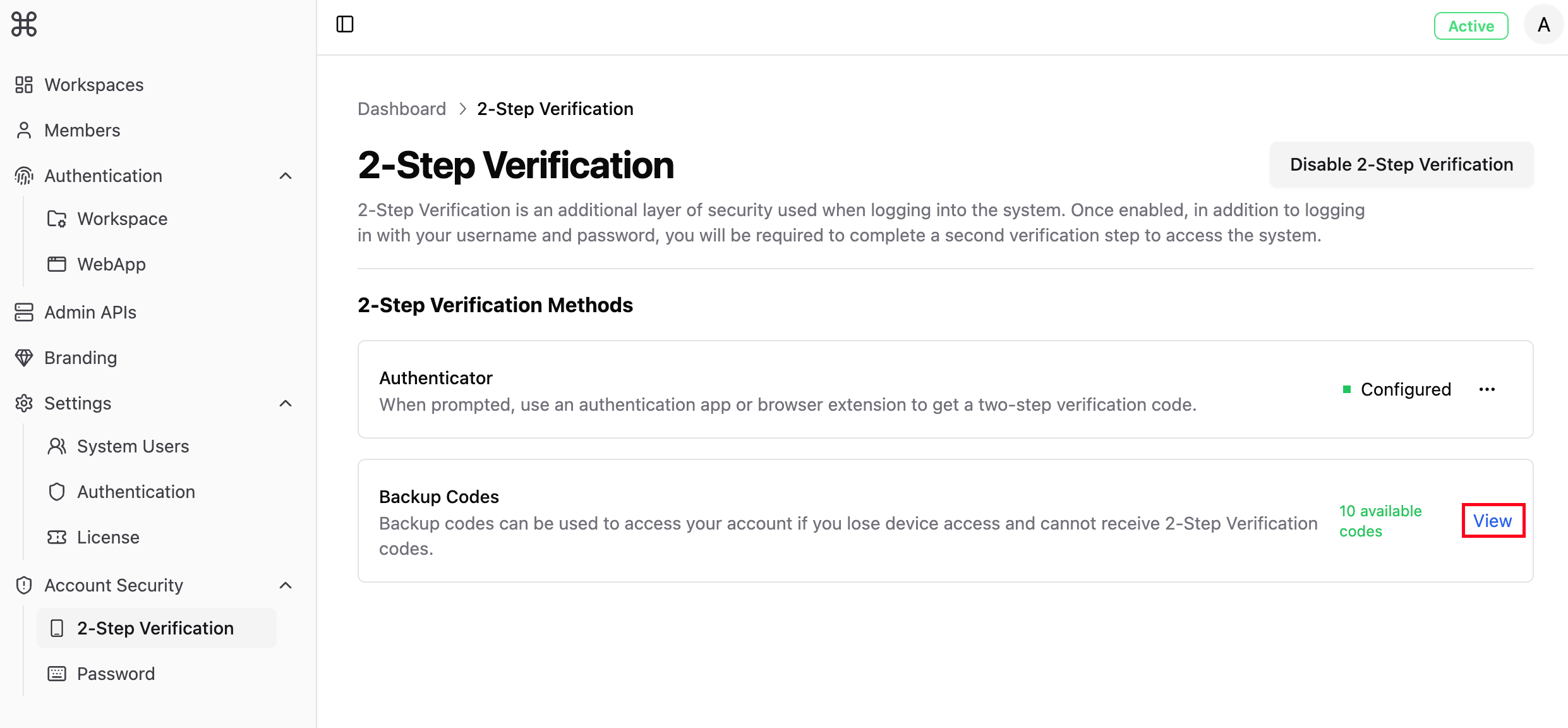 Backup codes are one-time use only; used backup codes will become invalid. If you need more backup codes, click “Regenerate”.
Backup codes are one-time use only; used backup codes will become invalid. If you need more backup codes, click “Regenerate”.
Enterprise Global
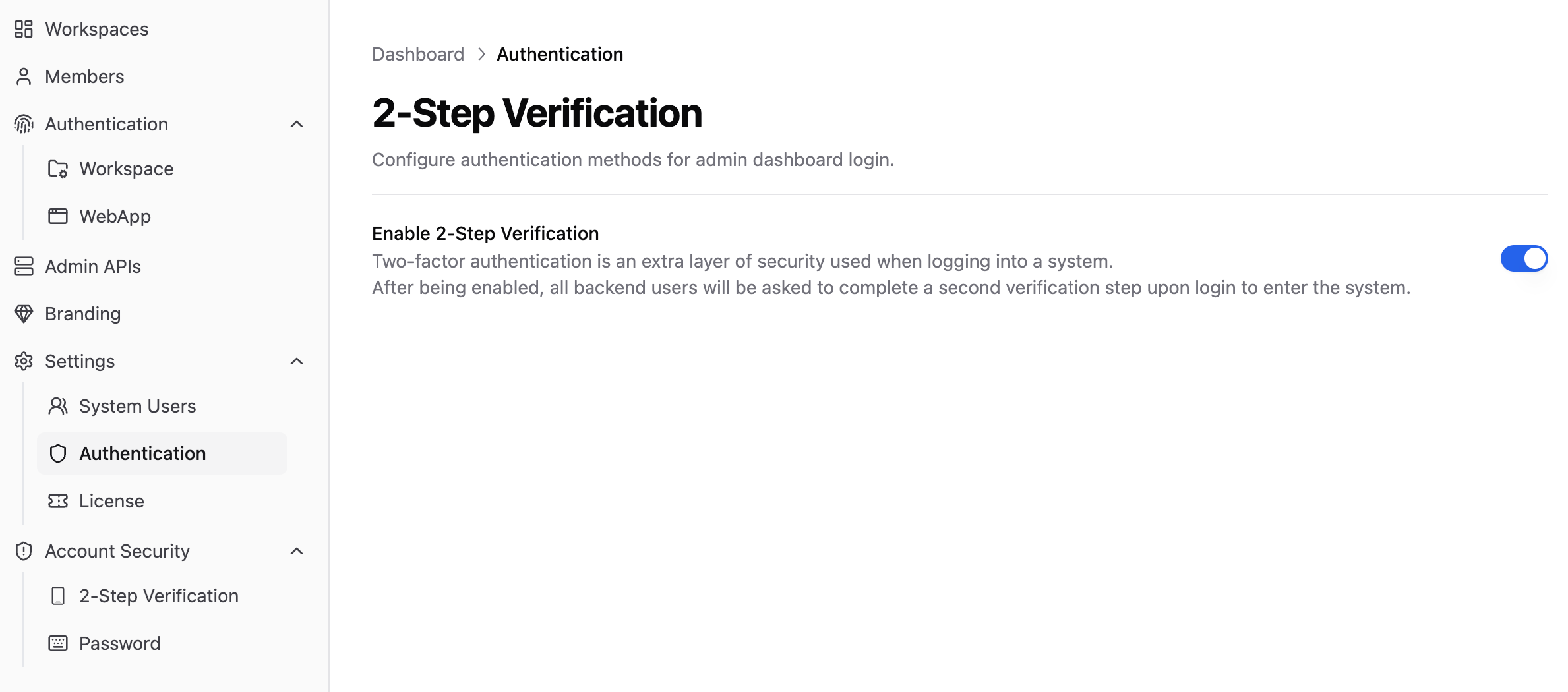
All system administrators have the permission to enable enterprise global two-factor verification; personal two-factor verification must be enabled before allowing enterprise global verification to be enabled.Go to Settings → Identity Authentication to enable enterprise global two-factor verification. Once enabled, each system administrator will be required to provide an additional verification code when logging in to the enterprise admin backend. If any system administrator has not yet set up two-factor verification, please refer to Common Issues.
Modify Two-Factor Verification
Access the enterprise admin backend, click “Two-Factor Verification”, click the “Edit” button in the menu options on the right side of the authenticator. In the pop-up verification page, enter the new six-digit verification code displayed by the authenticator to confirm identity and complete the modification.Disable Two-Factor Verification
Disabling two-factor verification removes the additional security layer, making accounts rely only on password protection, significantly increasing the risk of unauthorized access.
Personal Account
If the enterprise backend has enabled global mandatory two-factor verification, personal account two-factor verification cannot be disabled.Access the enterprise admin backend, click “Two-Factor Verification” → “Disable Two-Factor Verification”.
Enterprise Global
Access the enterprise admin backend, click “Settings” → “Identity Authentication” to turn off the two-factor verification button.When enabling, modifying, or disabling two-factor verification, system administrators will receive corresponding notifications in their email.
Common Issues
I lost the device with the authenticator, how should I log in?
If you forget or lose the original device, use the following methods to log in:- Use backup codes to log in: Select the “Use backup code” option on the login page and enter a previously saved backup code. Note that each backup code can only be used once.
- Contact other system administrators: If you don’t have backup codes, please contact other system administrators in the team to request temporary access or assistance in resetting two-factor verification settings.
Two-factor verification code is correct but system shows error, how to resolve?
Verification code errors usually have the following causes:- Time not synchronized: Authenticators generate verification codes based on time, ensure your device time is synchronized with standard time. Most smartphones automatically sync time, but if you have disabled automatic sync, please enable it in device settings.
- Verification code expired: Authenticator verification codes usually update every 30 seconds. If you enter the code when it’s about to expire, it may become invalid. Please wait for a new verification code to be generated before trying again.
- Device and account mismatch: Confirm you are using the correct authenticator and correct account to generate the verification code.
How to migrate authenticator after changing phones?
There are two methods to migrate the application:- Use in-app migration feature: Some authenticators (such as the latest version of Google Authenticator) provide account export/import functions, which can be used to migrate authenticator information to new devices.
- Reset two-factor verification:
- Use backup codes to log in to the system.
- Refer to Modify Two-Factor Verification, go to personal two-factor verification settings page, click “Edit”.
- Complete verification using verification codes generated by the new device.
How do administrators who have not enabled personal account two-factor verification log in after global mandatory two-factor verification is enabled?
When global mandatory two-factor verification is enabled, the login process for administrators who have not enabled two-factor verification is:- New administrators log in to the system using email and password (or SSO).
- The system will automatically detect that the administrator has not configured two-factor verification and provide two-factor verification operation guidance on the enterprise login page.
- New administrators need to download an authenticator application and complete two-factor verification setup according to the page prompts.
- After setup is complete, entering the six-digit verification code will allow new administrators to continue logging in to the enterprise backend.

