Administrator Guide
Audit Log
The audit log is used to record key operational behaviors within the system, supporting users in operation tracking, security auditing, and compliance analysis.
For further support, please contact technical support or the system administrator.
1. Feature Introduction
The audit log feature provides the capability to record and query key behaviors such as resource changes, permission operations, and configuration adjustments in the platform. The log has structured fields, supports precise filtering, querying, and exporting, helping enterprises identify potential risks and meet security compliance requirements. Typical application scenarios include:- Operation tracing and responsibility positioning
- Security policy audit and risk troubleshooting
- Compliance check and external audit support
2. Operation Instructions
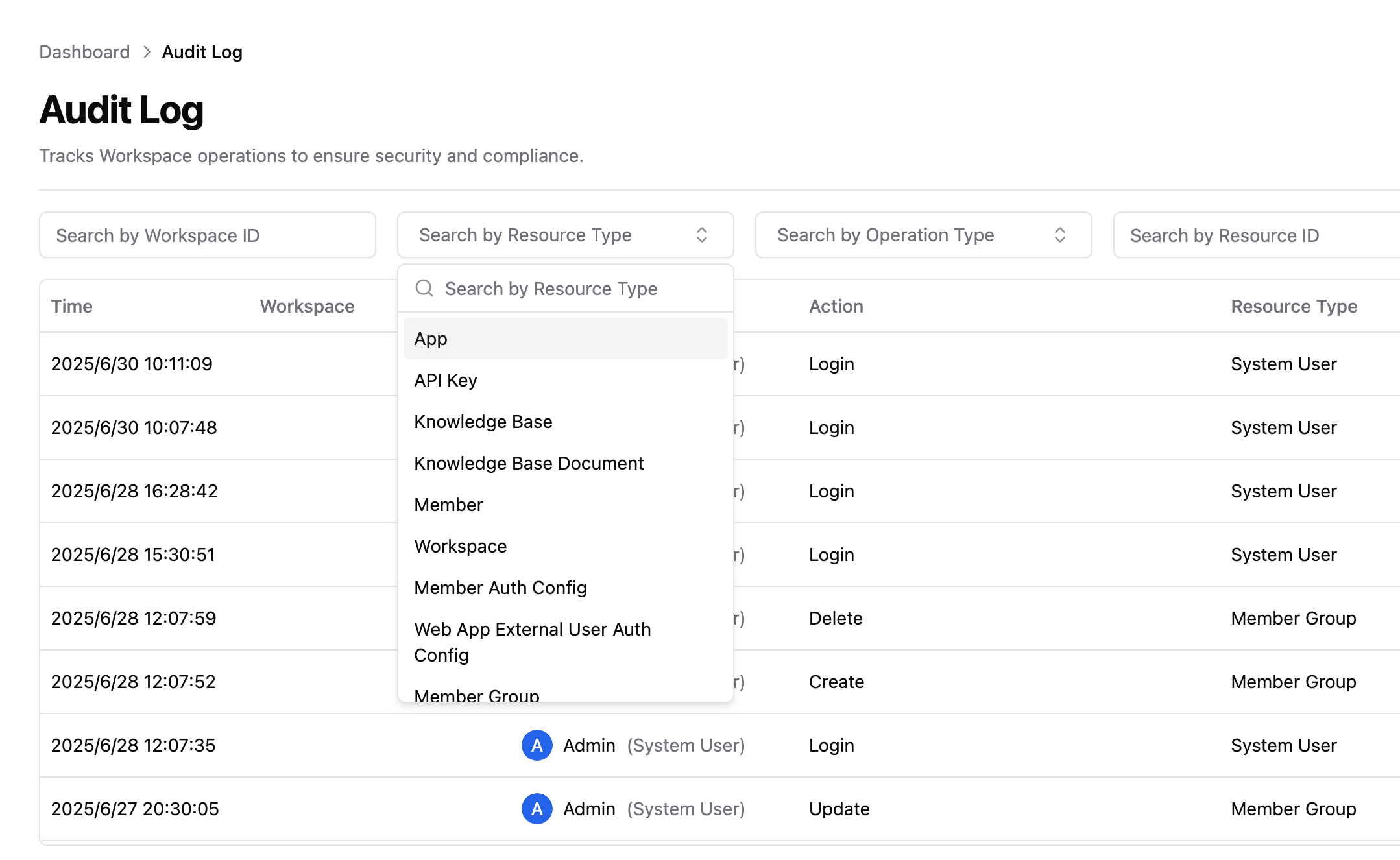
2.1 Access Path
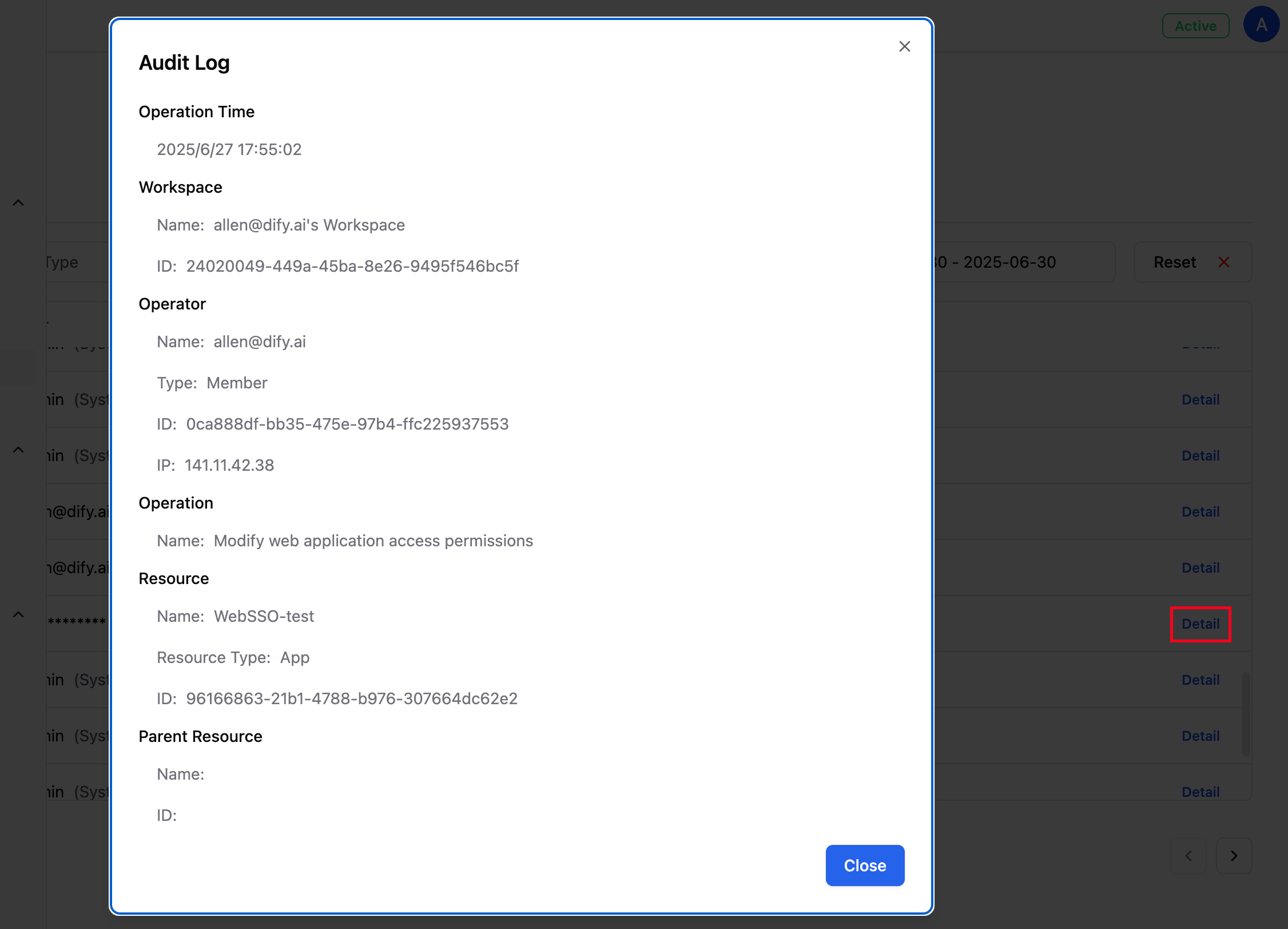
Enterprise Admin Dashboard > Audit Log.2.2 Log Structure and Field Description
| Field Name | Description |
|---|---|
| Time | The time when the operation occurred, accurate to the second |
| Workspace | The workspace to which the resource belongs (if applicable), including the name and ID |
| Operator | The member account, system user account, API Key, operator ID, and IP address of the operator who triggered the operation |
| Operation Type | The type of operation behavior (such as create, modify, delete, upload, etc.) |
| Resource Type | The resource category of the operated object (such as members, workspaces, applications, configuration items, etc.) |
| Resource Name | The specific resource name, which can be accompanied by the parent resource, for example: test.doc (TestDataSet), as well as the ID of the resource and parent resource |
2.3 Query Function Description
Optional filter conditions:- Workspace, search by workspace ID
- Resource type, for example: members, applications, authentication configuration
- Operation type, for example: create, modify, export DSL
- Resource ID, exact match of resource ID
- Time range, by default only supports the last 90 days


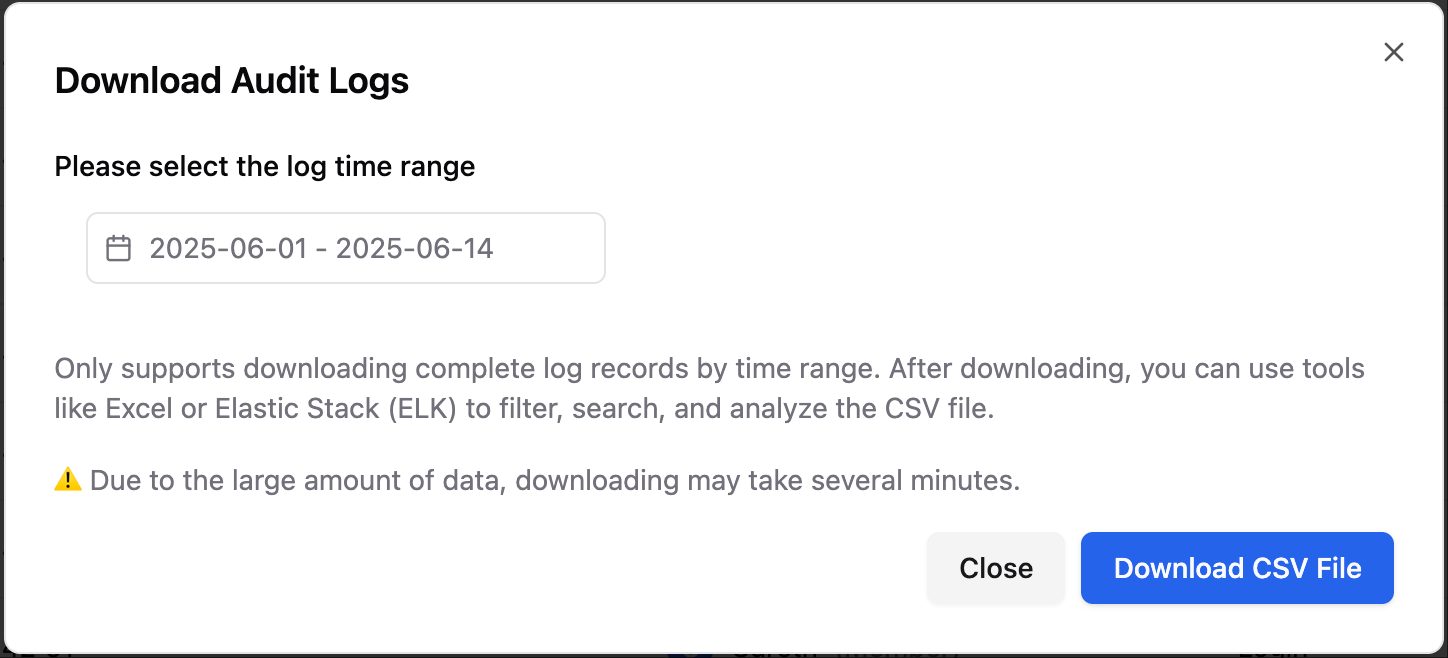
3. Download Log
3.1 Feature Description
To ensure query efficiency and system performance, logs older than 90 days will be automatically archived. Users can obtain them by downloading log files (CSV format).3.2 Operation Steps
- Click “Download Log” in the upper right corner of the page;
- Select the time range in the pop-up window (supports any historical time period);
- Click “Download CSV File”, and the system will start downloading the CSV file.
- If part of the data in the selected time range is still within the online query range, the system will package and download it together.
- The log file may be large in size, and the download time depends on the selected range and data volume, please be patient.

3.3 Data Analysis Suggestions
You can use the following tools to filter and analyze the exported CSV files:- Excel / Numbers: suitable for lightweight filtering and summarizing
- Notion / Airtable: suitable for structured visual management
- ELK Stack (Elasticsearch + Logstash + Kibana): suitable for large-scale log visualization, search, and alerting
Tip: The downloaded log is a structured CSV file, and the fields are consistent with online queries, which is convenient for subsequent analysis.
4. Operation Type Classification Description
| Operation Type | Description |
|---|---|
| Create | Creating workspaces, applications, knowledge bases, members, API keys, member groups, system users |
| Modify | Modifying configuration items, resource properties, renaming, etc., for example: authentication configuration in the enterprise admin dashboard |
| Delete | Deleting members, applications, workspaces, etc. |
| Enable | Enabling members |
| Disable | Disabling members |
| Login | Members logging into the workspace, system users logging into the enterprise admin dashboard |
| Export | Exporting files |
| Upload | Uploading files |
| Publish | Publishing applications |
| Import DSL | Importing DSL files of applications |
| Export DSL | Exporting DSL files of applications |
| Enable web application | Enabling the web application of an application |
| Disable web application | Disabling the web application of an application |
| Enable backend service API | Enabling the backend service API of an application |
| Disable backend service API | Disabling the backend service API of an application |
| Modify web application access rights | Modifying the access rights of an application’s web application |
| Modify access rights | Modifying the access rights of the knowledge base |
| Modify configuration | Modifying the synchronization settings of member groups |
| Invite | Inviting members from the workspace |
| Modify password | Modifying the password of a member or system administrator |
| Bind two-factor authentication | System administrator binding two-factor authentication |
| Enable two-factor authentication | System administrator enabling two-factor authentication |
| Disable two-factor authentication | System administrator disabling two-factor authentication |
| Generate backup code | System administrator generating backup code |
5. Frequently Asked Questions
Why can’t I view logs from 3 months ago?
For system performance considerations, only online queries of data from the last 90 days are provided. Please obtain historical data through the download log function.How to analyze after downloading the log?
It is recommended to use tools such as Excel, Notion to filter fields, or import into Elasticsearch for full-text search and chart visualization.Will the audit log be automatically cleared?
The audit log will be archived regularly according to system configuration, but it will not be actively deleted unless the administrator customizes a cleaning strategy.6. Data Security Description
The content of the audit log is only accessible to system users in the enterprise admin dashboard or users with corresponding permissions. The system ensures that log data cannot be tampered with and is retained and processed in accordance with enterprise data compliance requirements.For further support, please contact technical support or the system administrator.

